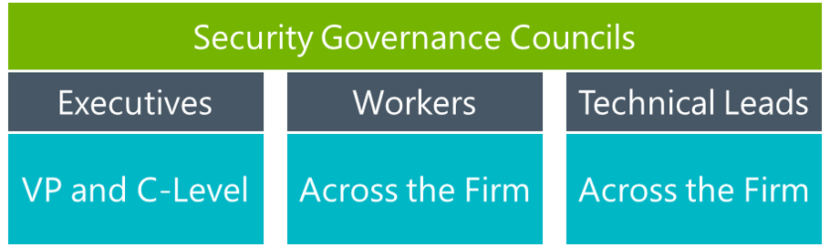
Security … Involving the Company Without Causing Rejection
Have you noticed that technology seems to follow a predictable cycle of decentralization, then centralization, then back to decentralization, and on it goes? The data/cyber security function within companies appears to be in, or heading into, a decentralization cycle. Many executives are frustrated with the state of security, partly because the technology that businesses rely upon is engineered in a way that makes things inherently insecure. In the headwinds of this challenge, brilliant people and […]